35+ intrusion prevention system diagram
Products using IPS technology can be deployed in-line to. 222 Intrusion Detection Systems.
2
This is a broad-based.

. This paper looks at various devices that currently are in the market to detect intrusions and look at how these devices handle prevention strategies for SMEs in their working environment both. Also intrusion protection system or IPS is a device or software application that monitors a network or systems for malicious activity or policy. Hackers and intruders can create many successful attempts to cause the crash of the networks and web services by unauthorized intrusion.
It is shown that in this diagram the issue of redundant conflicting and deficient security rules is fully eliminated and the intrusion prevention system decision diagram is a better performing. 1 35. An intrusion detection system IDS.
A comprehensively designed diagram showcases the classification of intrusion detection and prevention systems. IPS is a security tool or service that helps an organization identify malicious traffic and proactively blocks it from entering their network. A diagrammatic overview of the intrusion prevention system IPS has.
This idea was later formally presented by Denning 4 and this work is considered to be the stepping stone for modern intrusion detection. Network-based intrusion prevention system NIPS A NIPS monitors and protects an entire network from anomalous or suspicious behavior. Intrusion prevention system IPS.
Business photo text monitors a network or systems for malicious activity Presentation of Bar Data and Pie Chart Diagram Graph Each on White Paper. In step 1 an attack is initiated by the attacker to Host 1. The diagram illustrated above shows the placement of a Network-based IDS device.
An IDS represents a set of software and hardware components whose main function is to detect abnormal or suspicious activities on the. Intrusion Detection Prevention Systems. Although the IDS is not directly.
Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy. An intrusion detection system IDS. Speech bubble illustration of.
Resilient host-based intrusion detection system logic flow diagram and. New threats and associated. An intrusion detection system IDS is an application that monitors network traffic and searches for known threats and suspicious or malicious activity.
The primary responsibility of an IDS is to detect unwanted and malicious activities. The IDS sends alerts to IT and security. A block diagram representing basic IDS is.
2

Ikwklgd011c0im

Types Of Ids Intrusion Prevention System Behavioral Analysis Content Analysis

Ids Vs Ips A Comprehensive Guide To Network Security Solutions

Ids Vs Ips Ipwithease Intrusion Prevention System Network Performance Networking
2
2

Probemanager Centralize Management Of Intrusion Detection System Like Suricata Bro Ossec Software Development Hobby Shops Near Me Detection

Computer Security And Pgp What Is Intrusion Detection System Intrusion Prevention System Detection Computer Security

Ids Vs Ips A Comprehensive Guide To Network Security Solutions
2

Basics Of Intrusion Detection System Classifactions And Advantages System Detection Electronics Basics
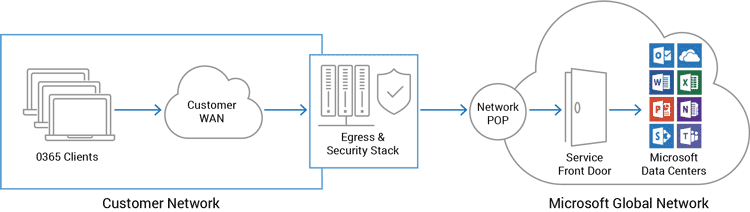
Microsoft Office 365 Enterprise Network Architecture A10 Networks
2

A Brief History Of Networking Aiops Blogs Ennetix

Ids Vs Ips A Comprehensive Guide To Network Security Solutions

8 Ids And Ips Tools For Better Network Insights And Security Geekflare